In-Flight Connectivity is the future that’s now according to a lot of people who love to be connected whilst at 10,000ft or above. However, The Register reports a disturbing note – that GoGo is creating and using “fake” Google Certificates, creating a “Man in the Middle” attack vector for those of you who browse online who are browsing videos and streaming sites.
Man in the middle attacks are documented here, but allow a person/device/certificate to “impersonate” another service, and gain the users trust.
Gogo is quick to defend themselves, stating this is a method of “traffic shaping” – a way to control the amount of bandwith used.
They state:
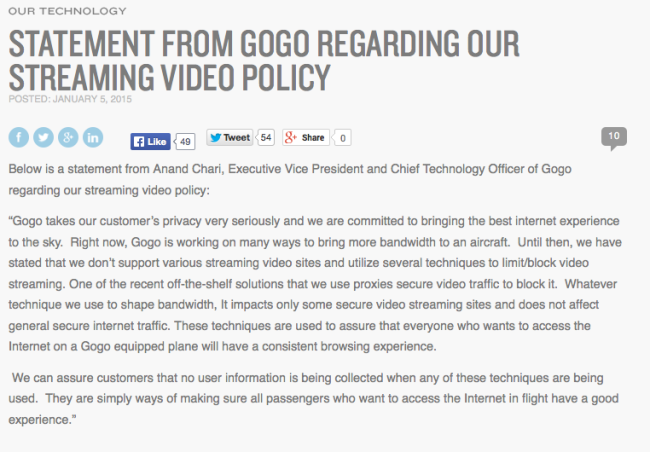
“Gogo takes our customer’s privacy very seriously and we are committed to bringing the best internet experience to the sky. Right now, Gogo is working on many ways to bring more bandwidth to an aircraft. Until then, we have stated that we don’t support various streaming video sites and utilize several techniques to limit/block video streaming. One of the recent off-the-shelf solutions that we use proxies secure video traffic to block it. Whatever technique we use to shape bandwidth, It impacts only some secure video streaming sites and does not affect general secure internet traffic. These techniques are used to assure that everyone who wants to access the Internet on a Gogo equipped plane will have a consistent browsing experience.
We can assure customers that no user information is being collected when any of these techniques are being used. They are simply ways of making sure all passengers who want to access the Internet in flight have a good experience.”
Man in the Middle seems an odd way to do this (as opposed to putting a banned IP list, banned website list, appropriate proxy services), and GoGo’s statement doesn’t comfort me as a user who uses HTTPS in a fair amount of applications (such as remote desktops, mail, etc), that they could inject a replacement certificate.
Indeed, this is a hammer to the nut situation.
A promise of “We can assure customers that no user information is being collected when any of these techniques are being used.” rings rather hollow to me, with a MitM vector allowing Gogo the theoretical access to the monitor and collect traffic sent between YouTube and any visitor who accepts the fake certificates.
Which is why your should always check the address bar and the certificate before accepting any dodgy certificate:
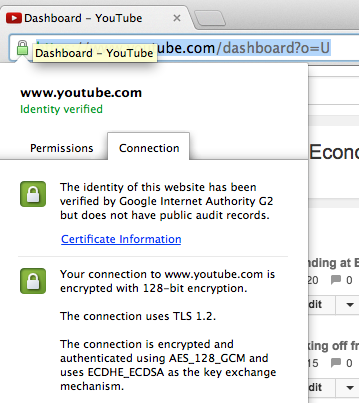
An example of a valid SSL certificate for YouTube
The “fake” Google one looks like this – as reported by Adrienne Porter Felt:
hey @Gogo, why are you issuing *.google.com certificates on your planes? pic.twitter.com/UmpIQ2pDaU
— Adrienne Porter Felt (@__apf__) January 2, 2015
To me… it leaves more question than answers… and as an answer to “blocking streaming services”, this doesn’t seem to be the best answer.
References:
- Gogo Statement – http://concourse.gogoair.com/technology/statement-gogo-regarding-streaming-video-policy
- The Register – http://www.theregister.co.uk/2015/01/06/gogo_ssl/
- ARS Technica – http://arstechnica.com/security/2015/01/gogo-issues-fake-https-certificate-to-users-visiting-youtube/
- Man in the Middle Attack – http://en.wikipedia.org/wiki/Man-in-the-middle_attack
Someone needs to report this to google.
Checking The ars technia writeup… It was a google engineer